CSAW CTF | BabysThird
This is a part of the Intro problem set, so hopefully just here to get easy points.
The file that the room gives you is a basic ELF 64-bit executable.
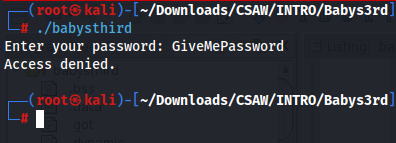
First I will just run the binary and do some basic poking around to see how I think the program works.
Well, not very eventful…..
BUT, we can start formulating ideas about how this programs logic works.
Input -> Check -> Output
Maybe we can abuse the Input buffer?
How is this program checking input? (Hard coded compare possibly?)
Now I like to do 3 main commands I use at the start when I am given a binary.
checksec
objdump
strings
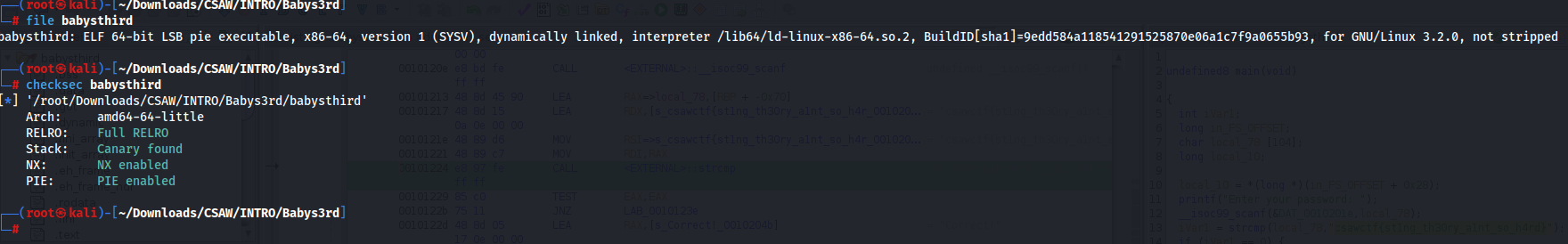
First off, I will run a checksec on the binary to see if there is anything fishy at a high level.
Checksec checks the properties of executables (such as PIE, RELRO, PaX, Canaries, ASLR, Fortify Source) and kernel security options (such as GRSecurity and SELinux).
Nothing of interest…
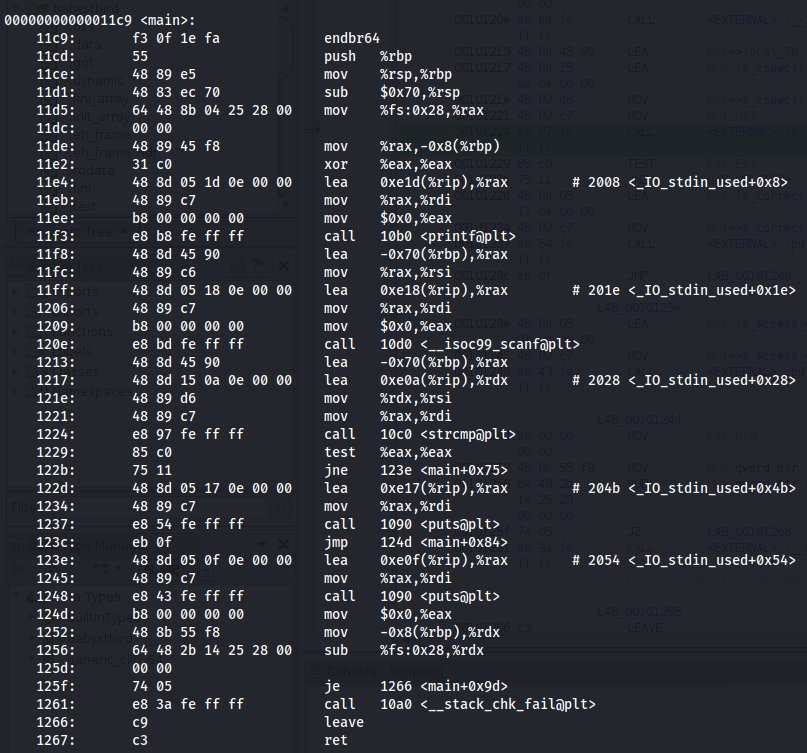
Moving on we do a quick objdump on the binary to see if we can see anything interesting about the assembly.
I see 2 mains lines of interest, Memory address (120e and 1224)
120e is a scanf that handles our input
1224 calls a strcmp
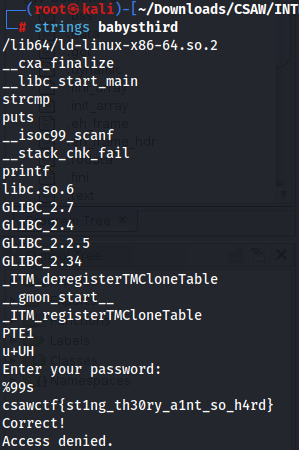
Now lets run strings and see if there are any plain text things we can see, maybe like what the strcmp() function is comparing.
Well I’ll be dammed if that isn’t a flag staring right at me! Lets input it back into the program to see if that’s all we had to do!
Easy Points in less than 5 min of work.