Patriot CTF | Guessing Game
Alright PWNing time!
Attacking binaries can be a very finicky thing. But with a little bit of persistence we can crack it wide open.
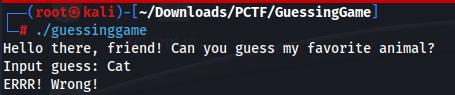
First thing I like to do is just run the binary and see how far I can get into the binary and see if I can guess at some logic.
Well….. not much going on in this binary.
Input-> Check-> Output-> Quit
First thoughts are we can either see what it checks against in a disassembler, or try and abuse a weak input system written in C.
fprint - Writes the printf to a file
printf - Output a formatted string
sprintf - Prints into a string
snprintf - Prints into a string checking the length
First lets do an objdump on this binary.
objdump -d guessinggame
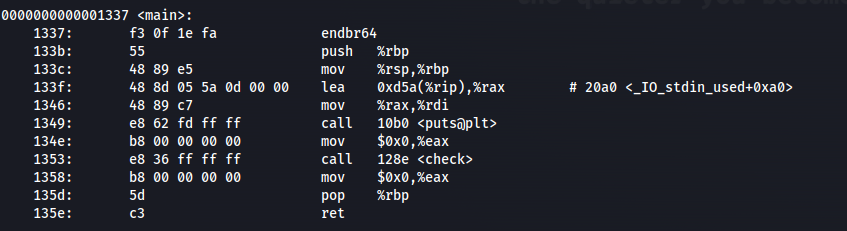
Main function of the program. Two main calls, puts() and check()
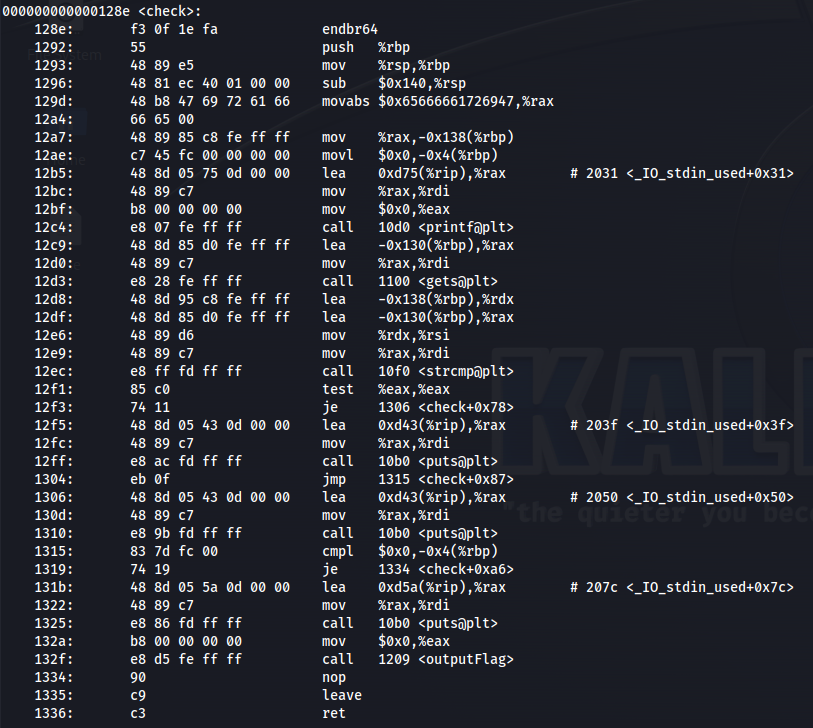
The check function writes to the screen and asks for an input. once the input is received, There is a call to strcmp() which compares your input to another variable.
Once we reach output flag it opens a file which in turn reads the flag into a variable and prints to the screen
Lets pop this in either GDB or Ghidra or BOTH!
I’m going with Ghidra just to get a good overview of the check function.
BEAUTIFUL! Lets look at the C code to a understanding on what’s going on here.
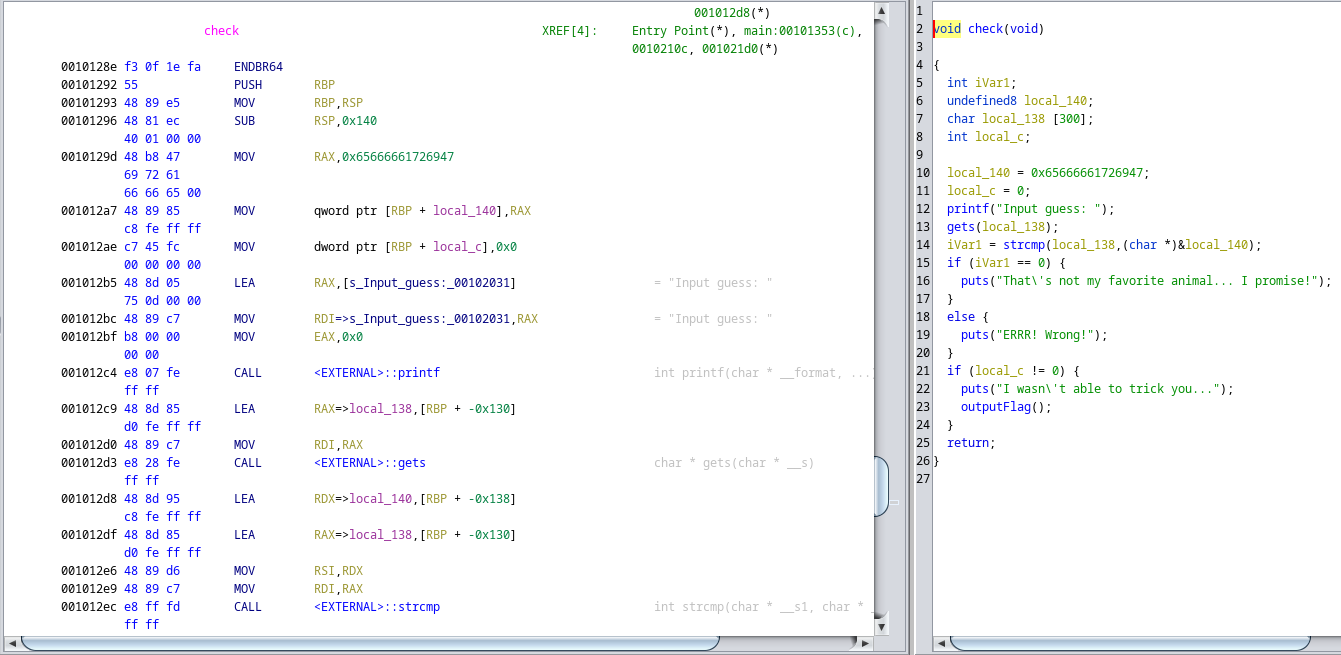
We see that there are a couple local variables created here when this function is called.
char local_138 [300]
This creates a char array with a size of 300 to store our input to be later used in the strcmp() function
local_140 = 0x65666661726947
Now this looks interesting! What could it be?? A flag? A memory address? Lets convert it to ASCII
Once we do that we get the string “effariG” But since we are using Little Endian its “Giraffe”
Have we gotten it! Sadly no. There is another variable that must not be equal to 0 to get past the second if statement to print the flag
if ( local_c != 0 ) -> outputFlag()
Well lets abuse that character buffer size of 300.
Nice! We just used a basic buffer overflow to run over and force the program to output the flag for us! The real flag is below.
-
PCTF{1_l0v3_g1raff35_85036769}